The WikiLeaks Member Confession: How do we break the Democrats' mailbox?
Lei Feng Wang: According to DeeperBlue, the original title is: "The WikiLeaks members talk about how to break the Democratic mailbox." In the article you will see: 1) "Confessions" from WikiLeaks members; 2) Why DNC's high-level e-mails must be compromised; 3) How we should protect our information security.

The name is not important. I am a WikiLeaks member. Let's talk about information security today.
On July 22, 2016, we publicized 19,252 e-mails from the Democratic National Committee (DNC) within 16 months. This content is enough for all TV channels in the world to broadcast this one on the same day. thing.
The e-mail clearly shows that the Democratic Party has done the following several things to ensure the victory of Hillary Clinton:
 A series of actions by the Democratic Party's top leaders to assist Clinton in cracking down on intra-Party and out-of-party opponents may have touched on the double bottom line of morality and law. (dark blue cartography)
A series of actions by the Democratic Party's top leaders to assist Clinton in cracking down on intra-Party and out-of-party opponents may have touched on the double bottom line of morality and law. (dark blue cartography)
At the same time, of the $61 million that the Hillary team called Democrats to raise, only 1% remained in the party's treasury, and most of the rest went to the Hillary team — the main purpose was to fight Sanders.
We put an atomic bomb inside the Democratic Party. If these things can be legalized, some big men will have to sit on the dock of the federal court.
The next day, Ms. Hilary, who was singing all the way, met Waterloo. The poll index was overtaken by Trump with a 3% advantage.

After the mail leaked, the Democratic high-level earthquake, Debbie Wasserman Schultz, chairman, Amy Dacey, chief executive, and Luis Miranda, public director, successively Resign. (dark blue cartography)
On the 27th afterwards, we also announced 29 sections of the Democratic Party’s internal recordings. Google, Facebook, and all the names that we can't call out, have listed us as dangerous websites. The media said that we may be employed by Putin. This is really funny.
However, all this is not an accident. In the following sections, I want to illustrate two issues from the perspective of information security:
First, why 100% of DNC high-level e-mail addresses will be breached.
Second, how should DNC strengthen their information security defense system.
| Why is 100% of the DNC high-level mailboxes compromised?Let's start with a few prerequisite settings:
On the battlefield of information security, there will always be confrontation between two groups of people: the offensive party will constantly try new methods of attack, and the defenders will adopt new protective measures.

The security attack and defense in the information system: keep it one by one.
The defense wants to ensure that information resources are only used by authorized legitimate users. The attacker must bypass the obstacles set by the defender and obtain information resources without authorization.
Although this sounds like some obvious “nonsenseâ€, this is exactly why DNC’s high-level mailboxes will be attacked by us. I use the following four points to make it clear:
First, the essence of information security is "verification." Verification needs to be done in every link.
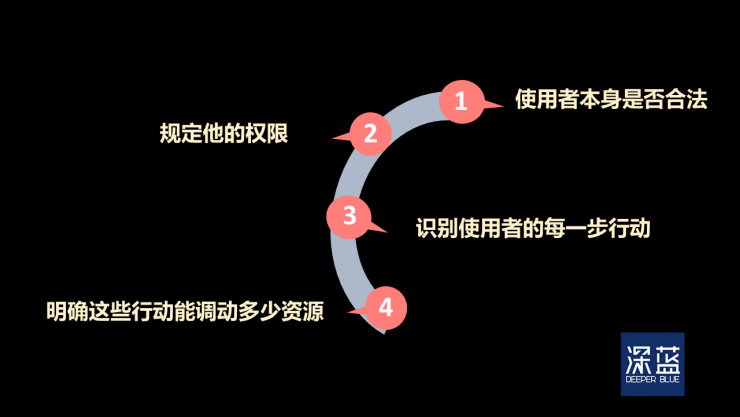
Four links to verify that information users can be trusted (dark blue cartography)
Every link in the verification will become an attack point for hackers. The stupid defenders generally ignore the "every link".
For example, one of the most common mistakes is that the defensive side often sets as long as the information user is trustworthy, so other elements do not need to judge.
In fact, the biggest security fallacy is to assume that everything is secure inside the system.
Just like the airport security inspection, the water before the security inspection cannot pass the inspection, but after passing the gate, everyone can drink water freely to buy water. As for whether the water is stolen, there is no problem with the water, and there are no people. Check again. Because of the airport security system, this system determines that anyone who passes the security check is safe. This is obviously a security hole.
For another example, hackers can also steal information from the user's actions. For example, everyone's common wireless keyboard is a security risk. The user's keystroke using the keyboard is a link that can be compromised.
The wireless keyboard periodically sends wireless signals. When a user hits a key, the hacker can listen to the typed content from within 250 feet, thereby stealing passwords, bank card information, or other sensitive data.
Some hardware vendors have ignored these loopholes. In July 2016, a wireless security company called Bastille had a security flaw that revealed that at least eight brands of wireless keyboards, including HP and Toshiba, had been monitored.
Second, the nature of information security, "verification," is doomed to be imperfect.
The information system is very complex. There are many internal branches. Each user action does not use only one branch of resources. In this composite step, there are always system loopholes that can be exploited by hackers.
The Patriot missile defense system that the United States has spent for decades and billions of dollars can theoretically intercept most missiles. However, in the Gulf War, Scud missiles easily broke through its line of defense. Its cost is only 1/100 of that of the Patriots.
The verification system can only be infinitely close to perfection, but not the most complete system in the world can trust.
Third, both the offensive and defensive players are asymmetric in terms of cost and efficiency, and the defense is in absolute disadvantage.
A sad reminder of the truth: The information defense is absolutely inferior in efficiency and cost, just as the cost of virus infection is always lower than the cost of vaccine development.

In the offensive and defensive campaigns of hackers and defenders, the cost of an attack is much lower than that of defense.
Destruction is always easier than construction and infection is easier than immunization. There is no invincible system, only hackers that can't be guarded against.
The so-called barrel law, that is how much water a bucket can hold depends on the shortest piece of wood. The security of an information system also depends on its weakest link.
In 2014, Sony’s PS network system was hacked and a large amount of personal data was stolen, resulting in a loss of US$170 million. For hackers, the cost is only a computer and a network cable. On the Internet, some of the software used to steal other people's accounts only needs a few tens of dollars to get it.
Fourth, on the battlefield of information security, people are the biggest source of uncertainty, and fools are always more.
In addition to systemic reasons, people are the biggest source of uncertainty. Information security incidents caused by people's negligence and fraud have accounted for about 85% of the total.
Check Point, the world's leading provider of network security solutions, conducted surveys on more than 700 IT professionals. The results are shown below:
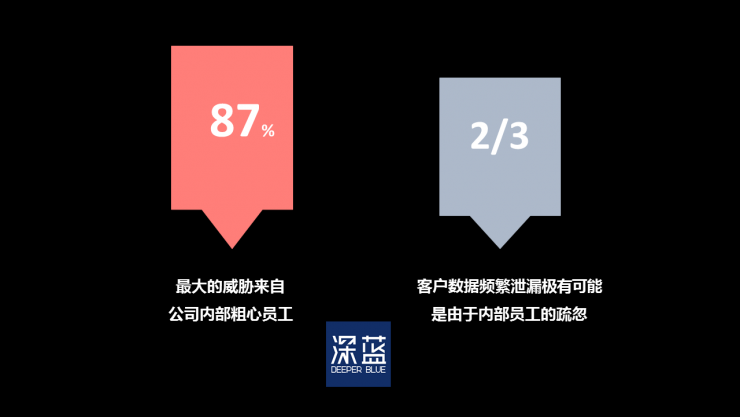
The negligence of people, rather than technological loopholes, is the main reason for the frequent occurrence of security incidents. (dark blue cartography)
Eighty-seven percent of respondents believe that the biggest threat comes from the company's careless employees; nearly two-thirds of respondents believe that frequent customer data leakage is most likely due to internal employee negligence.
In fact, as early as the autumn of 2015, information security experts inside DNC warned senior members of the party about its fragile internal network, and these suggestions were ignored. After a two-month investigation, the experts suggested in a report that DNC ​​should hire professionals, upgrade the system, and set up defense mechanisms that can track intruders.
The FBI has also repeatedly warned DNC's cyber security system: "There may be problems." In 2015, the FBI had urged some DNC personnel to check the internal system for signs of unusual activity, but DNC ​​found nothing.
Until April 2016, DNC executives began to pay attention to these warnings and hired private security firm CrowdStrike to rectify the system. However, we have been lurking for nearly a year in the internal network.
As one of our colleagues, the Romanian hacker Guccifer 2.0 described - Hillary's mail server is like "an open orchid, which is easy for anyone to break through."
You may want to ask me: Why did you choose to attack DNC executives?
Of course, you do not have to say our position is against the DNC. The DNC represents the interests of the Silicon Valley consortium, and we are pirates. We will do our best to undermine the chances of Hillary’s election—“Choose her is to choose endless warsâ€. But we do not talk about politics today.
Information Security As with security services, the price of the bodyguard depends on the value of the person/property being protected. The same is true for information security.
The industries that hackers like to attack most are value-intensive areas such as finance, such as government. Of course, these areas are also the most willing to pay for information security - only the big guys are most willing to pay for fear.

Unlike the purely destructive behavior of early years, today's hacker attacks are more profitable.
In June 2016, IBM and the Ponemon Institute released the report “Data Leakage Cost Study 2016: Global Analysis†and conducted research on 383 companies that had experienced data breaches. The report shows that from an industry perspective, information loss in the public sector and educational institutions is at a minimum, and financial and medical institutions are the hardest hit areas for information security.
The higher the value, the more willing we are to take risks. The DNC's high-level mailboxes are related to the political structure of the entire country, especially at the election juncture, and have thus become our goal all along.
| DNC really stupid, if I ......We can easily break DNC's high-level e-mails. Not so much as we do. They are stupid.
DNC's IT system security measures are extremely backward. In May 2016, we successfully invaded DNC's network system several times and exposed a series of documents (including donor names, occupations, geographical locations, and amounts) of DNC's main donor information. However, their system still does not update the encryption.
The evolution of IT systems and technologies has led to changes in security requirements: the disappearance of boundaries and penetration have become the norm.

In the past, as long as you kept your "city gate", you can ensure that the system is completely safe.
In the past, IT systems were like ancient castles. The system and the outside world could only communicate through limited “gatesâ€. Now that the system has become more interconnected, the “city walls†of the castle have disappeared, and they have developed into modern cities that are constantly expanding outwards and have all-round internal connections. People cannot continue to use the method of building high walls to deal with information security issues without affecting the normal work of information systems .
The disappearance of the border changes the attack pattern. Before the destruction of the information system as the army siege, directly from the outside to break through, pay attention to a blow. When the boundary disappeared, the means of attack evolved into a means of “infiltration†used by espionage. It has long been lurking inside the information system and waiting for opportunities.
If I'm responsible for DNC's information security, the following four things I will do in the first time:
First, it is proposed to establish a zero-trust network model to dilute security assumptions.
The DNC's security system is very traditional. When accessing DNC members' mailboxes, the system will distinguish between internal and external networks. If the address is accessed from the internal network, users will be given a higher level of trust and have more rights to read system information.
This practice of distinguishing between internal and external networks exists by default as a “gatekeeper†and “certainly secure within the cityâ€. Just like the example of airport security that we mentioned earlier, the airport terminal’s default security gate is absolutely safe. For this traditional boundary security model, hackers can easily access internal applications as long as they can be integrated into the system.
Only by constructing a "zero trust" framework can we break the difference between internal and external networks.
There should be no absolutely safe areas or elements for the system. In fact, more and more visits now occur on the mobile and cloud sides, and the borders are increasingly blurred.
Regardless of where Hillary and other DNC executives are located, they must use the same access method in their campaign office, rally site, or at home: All connections to the mailbox must be encrypted; all networked devices, including laptops and cell phones, are You want to keep the trust information and the device number in the server.
Under the "zero-trust" model, attacks that have penetrated into the interior can no longer enter the intranet as if they were no one else. Google began to apply this idea five years ago to improve the security model and they called it BeyondCorp.
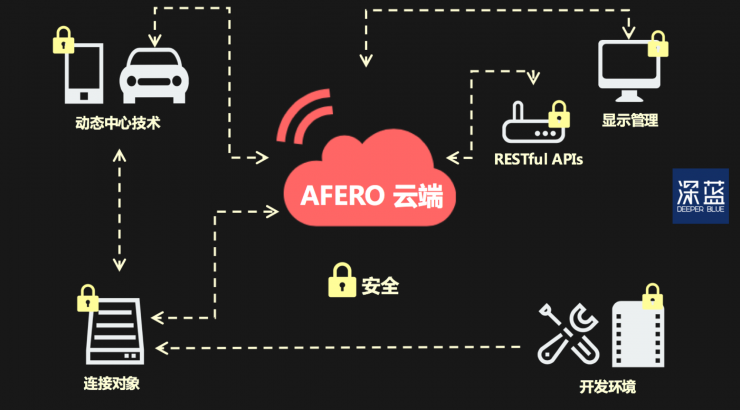
Diagram of the security architecture of BeyondCorp. (dark blue cartography)
Since 2014, Google has gradually migrated all its application components to BeyondCorp, and has published the document BeyondCorp: Google's Design to Deployment. Other companies that have plans to deploy a "zero-trust" architecture can follow the document to follow up the deployment. At present, Coca-Cola, Verizon Communications and Mazda Motors are all making similar transformations.
After proof, the "zero-trust" system will not affect the user's ease of use after canceling the "trust privilege" of the intranet. The only downside is that the workload of the information security team may increase dramatically.
Second, introduce machine learning and artificial intelligence tools.
Don't think about doing chess with machine learning and artificial intelligence. They are even more powerful weapons against hackers and can build smarter "immune systems."
What is the best thing computer can do? It is a matter of repetition. In simple terms, machine learning can monitor system risk more quickly and accurately than humans by analyzing vast amounts of data. As I said before, don't forget that people are the biggest source of uncertainty in the battlefield of information security, and there are always more fools . Computers are sometimes more reliable than humans.
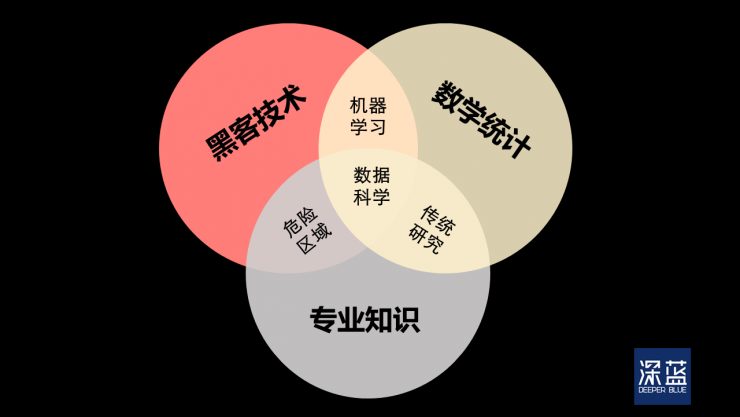
The application of machine learning technology extends security tools, and "machine learning itself is the sum of hacking technology, mathematics, and statistics knowledge" - Drew Conway, American data scientist. (dark blue cartography)
Cylance is a worthy information security startup founded by the former CTO of the world's largest professional security technology company, McAfee. They developed a method based on machine learning to detect system hazards, claiming that 99% of intrusive malware can be detected, compared to 40% for traditional methods.
If machine learning can identify risks more accurately, artificial intelligence tools can propose solutions more intelligently: instead of humans, research the vulnerabilities discovered by the system, issue patches, and finally complete the deployment to achieve system security and automation.
In this regard, the most recent frontier is PatternEX, a US start-up company. They have launched a "virtual security analyst" intelligent platform that can track and understand system operation data in real time, and finally simulate the intuition of human analysts to form a threat prediction model. In addition, the US Department of Defense has also established a dedicated research department, DARPA, to create an artificial intelligence system that integrates "automatic detection - autonomous repair".
Third, build a security awareness forecasting system.
In the face of security threats, alarm systems and repair tools are still far from enough. Therefore, in addition to upgrading protection tools, a parallel security risk awareness system needs to be built.
In short, the security risk advance awareness system is like an accurate weather forecast system. Meteorologists read the data collected by radars, satellites, etc. to understand the current atmospheric conditions and provide weather forecasts based on this.
In security-aware systems, security tools such as firewalls, anti-virus software, and intrusion detection systems (IDS) are radars. The data they detect can reflect the current state of the system and is the basis for the perception system to make short-term predictions.
The working principle of the security awareness system is similar to the cognitive process of the human brain in understanding external information, including the “acquiring information—understanding—future predictionâ€. The following diagram shows:
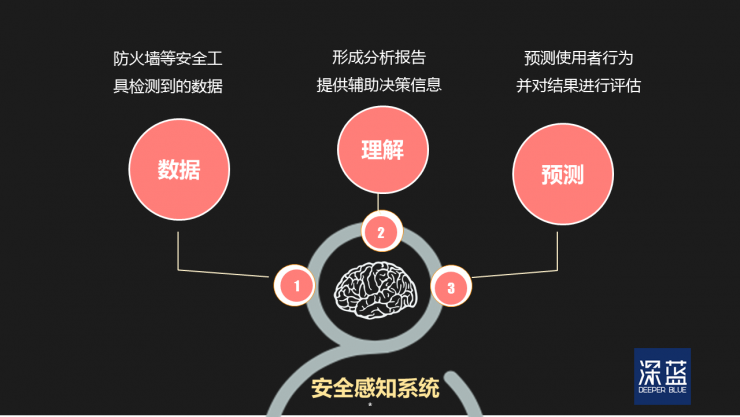
A set of security awareness systems:
Data sources: data detected by security tools such as firewalls, anti-virus software, and intrusion detection systems (IDS);
Understanding of the status quo: form an analysis report, including the operation status of various network devices, network behavior, and user behavior, etc., and provide auxiliary decision-making information;
Short-term predictions: Map the current situation to the future, predict user behavior, and evaluate the results.
Like the human brain, the security awareness system is complex and consumes many resources. The data end needs powerful data mining and processing capabilities. Only 20% of the massive data generated by the system operation can be directly used. Whether or not the remaining 80% of the data can be structured and utilized will determine the response speed of the information security team in the face of security threats.
To improve the system's ability to understand and reason, you need to rely on machine learning, artificial intelligence, etc. to imitate the working methods of the human brain, understand the current system status, and deduce changes in the system's operating conditions in the short term.
Big manufacturers have already tried it. In May 2016, IBM introduced the "IBM Watson for Cyber ​​Security" tool that enables rapid correlation analysis of detected anomaly data - such as the number of abnormal behaviors, files involved, and assets, etc. At the same time, it generates its own "judgment point of view" and supporting details. This "cognitive security" tool has a great advantage in data structure and can handle 200,000 security event data per day.
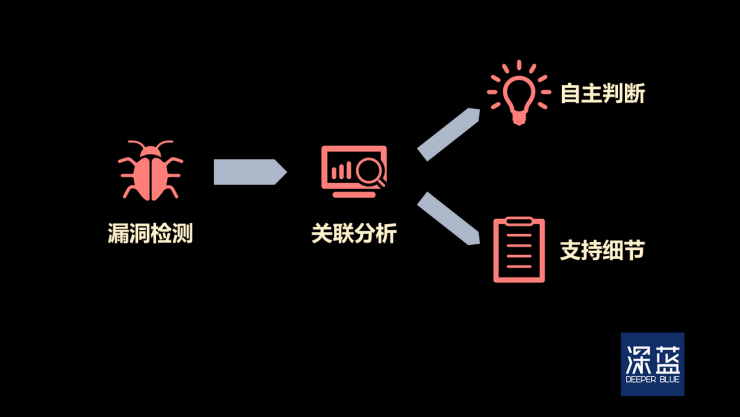
IBM introduced the IBM Watson for Cyber ​​Security workflow. (dark blue cartography)
Fourth, covering IoT devices
As mentioned earlier, hackers can steal information from the user's actions. For example, common wireless keyboards are a security risk.
In addition to the commonly used computer handsets, various networking devices used by the DNC team must be incorporated into the built security system. For example, the smart TV of the campaign headquarters, the iWatch and various wristbands of staff and volunteers, and even the Hilary's treadmill that can upload athletic data, etc., may be hidden points.
The safest place is the most dangerous place. One hundred and one sparse, easy to cause a disaster.
Hackers can easily start with smart devices as a springboard for collecting information, capturing security credentials, and launching subsequent attacks. However, most people, whether manufacturers or users, are completely unaware that these networked devices are the weak links of IT systems.
Cloud services can solve the problems of these smart devices—hosting multiple connected devices to the cloud and encrypting all data transmissions on the device and the cloud.
For example, in the United States, Afero , a start-up company that provides IoT cloud security infrastructure, smart devices can use their embedded Bluetooth module (ASR-1) to achieve a secure connection between all devices.

Afero's cloud platform is the core of the entire system. (dark blue cartography)
The above is my conscience as a conscience hacker for DNC from the perspective of information security.
People are willing to spend more and more money on information security - people pay for fear. In 2015, the global information security expenditure was 75 billion U.S. dollars, and the U.S. government spent 8.6 billion U.S. dollars. JP Morgan's annual information security expenditure is 500 million U.S. dollars, and the Bank of Ameirca's information security budget is "no limit."
I hope everyone can feel value for money.
Lei Feng network (search "Lei Feng network" public number attention) Note: This article is deep blue DeeperBlue authorized Lei Feng network release, reproduced please contact the authorization, retain the source and the author, not to delete the content.
Micro inverter is a small inverter used in solar power generation systems, its main function is to convert the direct current generated by a single Solar Panel into alternating current. Unlike traditional centralized inverters, microinverters are usually equipped with one per solar panel, that is, each solar panel has an independent microinverter.
Main effect:
1. Individual control: The microinverter provides independent conversion control for each solar panel, which means that each solar panel can optimize its power output individually. This maximizes the power generation efficiency of the solar panels since shading or other influences only affect the power generation efficiency of individual panels, not the entire array.
2. Reliability: Since each solar panel is equipped with a micro-inverter, even if one of the inverters fails, the other panels can still work normally, thereby improving the reliability of the entire system.
3. Flexible installation: Micro-inverters are usually small and can be installed near solar panels without being concentrated in one location, so installation is more flexible and convenient.
Differences from other inverters:
1. Individual control: Compared with traditional centralized inverters, microinverters provide independent conversion control for each solar panel, enabling each panel to reach its maximum power output.
2. Fault isolation: The micro-inverter has the function of fault isolation. Even if one of the inverters fails, other panels can continue to work without affecting the operation of the entire system.
3. Installation method: The micro-inverter can be flexibly installed near the solar panel, and does not need to be concentrated in one location, so the installation is more flexible and convenient.
4. Applicable scale: micro-inverters are usually used in small-scale solar power generation systems, while traditional centralized inverters are suitable for larger-scale photovoltaic power plants.
Overall, the main role of microinverters is to individually control and optimize the power generation efficiency of solar panels and improve the reliability of the system. Compared with traditional centralized inverters, it has some advantages in terms of flexibility, fault isolation and applicable scale.
grid tie micro inverter, off grid solar micro inverter, hoymiles microinverter price, micro inverter solar system, solar system with micro inverters
Ningbo Autrends International Trade Co., Ltd. , https://www.china-energystorage.com