Five Countermeasures for Addressing Internet of Things Security
IoT devices can generate reasonable data for the tracked activity and store it for retrieval and processing on other devices. For example, advanced platforms such as IFTTT (If-This-Than-That) have introduced more open cross-device services, enabling end users to interconnect online digital services with the offline physical world.
However, while the Internet of Things era has many opportunities, it also faces huge security risks, such as the leakage of key business information and the false alarms that cause important incidents to be handled improperly. Therefore, the basic security issues of the Internet of Things should not be ignored, and a large investment in security measures and resources must be increased.
Here are some security measures to consider:
First, expand security coverage
A few years ago, the Wifi coverage area in most organizations was limited to workplaces, such as office areas and tea breaks, but today smart devices are out of the work area. It is also easy for malicious users to expand their coverage area and may even try to tamper with the device to access the network and resources within the enterprise. Combating such incidents requires going beyond traditional security and focusing on the extension of endpoints and coverage areas.

Second, prioritize resources
Generally, smart devices have limited resources for resources in the initial stage, but gradually find more network resources during the upgrade process. When many devices access network resources at the same time, it will cause network congestion and resource crisis. For example, when a large number of smart devices are updated in a limited channel at the same time, it will have a negative impact on network performance. In order to better control this phenomenon, some mechanisms must be taken to monitor and limit, setting a priority level and usage time for each device.

Third, verify the equipment manufacturer background
There are currently hundreds of suppliers related to the Internet of Things, many of which are new companies that are not known. These companies often have no experience with information security and may even neglect security to reduce costs or launch products as quickly as possible. To ensure security, users are not recommended to experience new devices on the network at will. Before using a new device, verify the manufacturer's details and be familiar with how the device is operating and transmitting data.
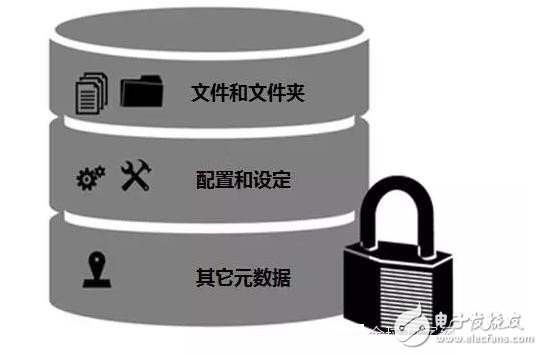
Fourth, to ensure the security of data storage
The increase in connected devices can result in a multiplication of generated data, including real-time data in files and folders, configuration and settings, and various metadata. In order to process various data, it is necessary to have a larger storage capacity. If you use cloud-based storage, you should avoid making unnecessary data occupy a large amount of valuable storage areas and occupy data transmission bandwidth.

5. Hiring professionals to solve problems
Based on the current state of the Internet of Things devices, access to network resources, protocols, and ports must be controlled, so comprehensive management of networked devices has become a difficult problem. In order to improve the security and compliance of data, it is strongly recommended to hire a security consultant or network security expert to develop a comprehensive security strategy.
electronic accessories for Silicone
Electronic Accessories For Silicone,Silicone Keyboard,Silicone Keyboard Covers,Silicone Keyboard Protector
Nantong Boxin Electronic Technology Co., Ltd. , https://www.ntbosen.com