Introduction to common video encryption technologies
The paid-to-watch video model is the core business of many platforms. If the video is recorded and spread illegally, the paid business will be seriously threatened. Therefore, the technology for encrypting video services has become particularly important.
The video encryption mentioned in this article is to make the video to be protected cannot be downloaded easily. Even if it is downloaded, it is the encrypted content. Others will need to pay a very high price to unlock the encrypted content.
There are two common video encryption technologies
Anti-theft chain: a URL with anti-theft chain signature. The signed URL can cooperate with the security mechanism of the streaming server. The use authority of the URL can be set on the designated APP or player. Malicious third parties can also get the URL. Cannot use and play;
Streaming media encryption: The video content itself is encrypted by a symmetric encryption algorithm, and the user obtains the encrypted video content. The authenticated user can obtain the key to decrypt the video and play it on the client after decryption. In this way, the process is complicated to implement and will bring more calculations.
In actual application scenarios, two technologies are generally used together. The two encryption technologies are introduced below.
One, anti-leech
1. Referer anti-theft chain
Referer is a part of the request header in the HTTP protocol. When a browser sends a request to a web server, it will usually bring a Referer to tell the server which page it is linking from. Based on this, the server can obtain some information for processing. If the refer information is not from this site, block access or jump to other links.
Nginx anti-theft chain configuration: such as the configuration method for file types.
Program Listing 1 Nginx anti-leech configuration

This method is to add in the server or location section: valid_referers none blocked, where none represents an empty source, that is, direct access, such as opening a file directly in a browser, and blocked represents a source marked by the firewall, *. zlg.cn means all subdomains.
The above means that all sites from zlg.cn and domain names containing zlg.cn can access the current site's pictures and video files. If the source domain name is not in the blocked list, a 403 will be returned to the hacker.
2. Token anti-theft chain
Token anti-theft chain signs time-related strings, and transmits the time and signature information to the CDN (Content Delivery Network) node server in a certain way as a basis for judgment, and the CDN node will base on the encrypted form of the URL , Take out the corresponding expiration time and compare it with the current server time to confirm whether the request has expired. If it expires, it will be rejected directly; if the time has not expired, the CDN node will calculate the value and URL according to the agreed signature algorithm and ciphertext Compare the original encrypted string in; after passing, the request will be considered legitimate. Illegal requests can be taken to prohibit access or other actions.
The process is shown in Figure 1 Token anti-theft chain process.
The client business server generates the verification information, and the business server is responsible for the generation of the verification information. The specific encryption process needs to confirm the following items.
Confirm the format of the expiration time, the default is the UNIX timestamp format;
Confirm the ciphertext in the verification information, and the user needs to agree with the CDN platform to calculate the verification information;
The parameter added when confirming the verification information, the default is the path part of the URL;
Calculate the verification information according to the algorithm description above, where the verification parameter in the request URL is _upt.
CDN node verification process
Resolve the expiration time according to the agreement, compare it with the current CDN node server time, and confirm whether the request has expired;
According to the algorithm calculation method agreed above, after calculating the MD5 encrypted string, compare it with the encrypted string in the URL to verify whether the encrypted string is consistent;
If the above two steps are verified, the request will be considered legitimate. At this time, the CDN will request the resource to respond to the client, otherwise it will be considered an illegal request and directly respond to HTTP status code 403.
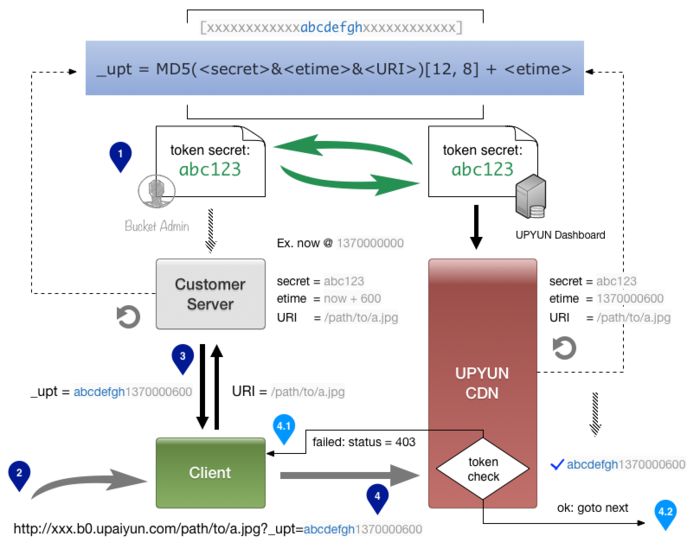
Figure 1 Token anti-theft chain process
Two, streaming media encryption
1. Common applications and streaming media transmission protocols played by browsers are
HLS: Apple's MP4 fragmentation transmission protocol based on HTTP protocol, which can be used in on-demand and live broadcast scenarios. HLS is currently the most mature streaming media transmission protocol that supports streaming media encryption and can be applied in the browser. HLS natively supports encryption. Has the following advantages:
Built on HTTP, easy to use, low access cost;
Sharding technology is conducive to the implementation of CDN acceleration technology;
Some browsers natively support, support on-demand and recording.
RTMPE: FLV block message transfer protocol based on TCP, used for Flash client. Use industry standard basic encryption consisting of Diffie-Hellman key exchange and HMACSHA256. When transmitting data, RTMPE generates a pair of RC4 keys. One key encrypts the data sent by the server, and the other key encrypts the data sent to the server. RTMPE prevents third-party applications from listening to data transmission between the client and the server;
HTTP-FLV: FLV block tag transmission protocol based on HTTP long connection, RTMP is encapsulated on HTTP protocol, which can better penetrate firewalls, etc., and can be used in on-demand and live broadcast scenarios.
The core of the streaming media encryption technology is to use a symmetric encryption algorithm for each small piece of video, encrypt the client at the server and decrypt it, and only the user who passes the authorization verification can get the key to decrypt a small piece of video.
The reason for choosing symmetric encryption is that streaming media requires strong real-time performance and a large amount of data. The calculations of asymmetric algorithms are relatively complex and low in efficiency, and are suitable for encrypting a small amount of data. The efficiency of symmetric encryption is relatively high, so symmetric encryption is preferred for streaming media encryption.
Since HLS encryption is currently the most mature and stable, only this encryption scheme is introduced.
HLS consists of two parts, one is .m3u8 file and the other is .ts video file (TS is a video file format). The whole process is that the browser will first request the index file of .m3u8, then parse m3u8, find the corresponding .ts file link, and start downloading, as shown in Figure 2 HLS encryption process below.
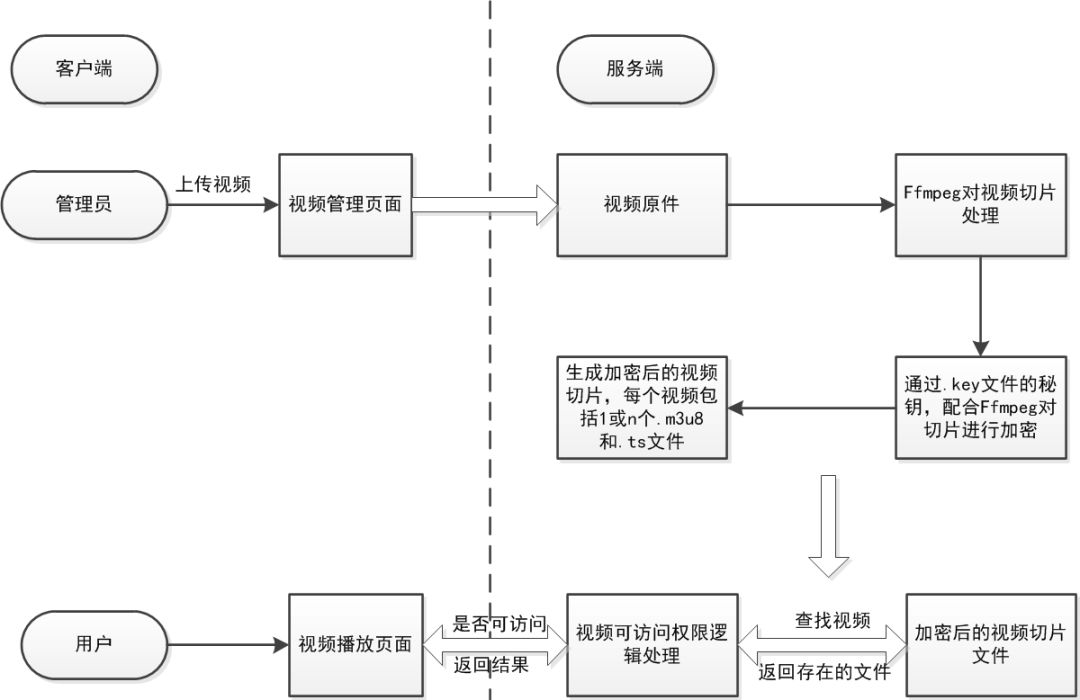
Figure 2 HLS encryption process
The m3u8 file is a text file. When HLS encryption is turned on, the content is roughly as follows.
Program list 2 m3u8 text content
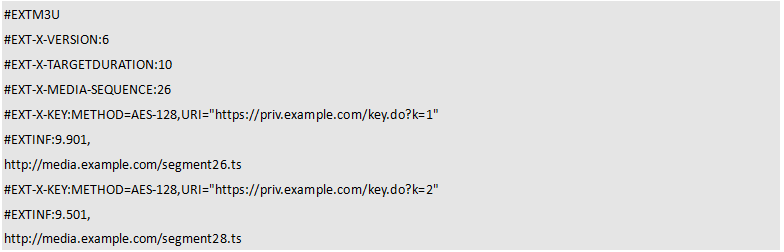
This file describes the URL of each TS segment, but these segments are encrypted content. To restore the original content, you need to
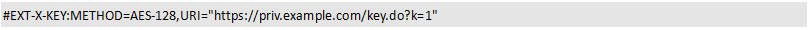
The URL https://priv.example.com/key.do and the symmetric encryption algorithm AES-128 are parsed to obtain the decryption key. After the password is obtained from the URL, the original content is decrypted on the client.
2. The following tasks need to be completed after enabling HLS encryption
For each TS need to request to obtain the secret key;
Need to provide an authentication service for the client to obtain the key;
It is necessary to perform symmetric encryption decryption calculation for each TS.
Based on the concept of mutual benefit and win-win, most of the audio and video materials in zlg.cn currently do not use anti-leech and streaming media encryption technologies. All partners can use zlg.cn's audio and video data links on their websites. If zlg.cn uses the above-mentioned anti-leech and HLS streaming media encryption technology to protect part of the confidential information, it will have a good protection against unauthorized third parties.
The first protection: the link from zlg.cn added by a third party on its website will be inaccessible and will directly jump to the 403 webpage or other webpages, such as the zlg.cn homepage.
Second protection: For video resources, the file obtained by the third-party player is a .m3u8 text file. After parsing, the encrypted slice .ts file and the encryption scheme can be obtained, but because there is no authorization, the secret key cannot be obtained. Therefore, the video resource cannot be decrypted and played.
ZGAR Vape Pods 5.0
ZGAR electronic cigarette uses high-tech R&D, food grade disposable pod device and high-quality raw material. All package designs are Original IP. Our designer team is from Hong Kong. We have very high requirements for product quality, flavors taste and packaging design. The E-liquid is imported, materials are food grade, and assembly plant is medical-grade dust-free workshops.
From production to packaging, the whole system of tracking, efficient and orderly process, achieving daily efficient output. WEIKA pays attention to the details of each process control. The first class dust-free production workshop has passed the GMP food and drug production standard certification, ensuring quality and safety. We choose the products with a traceability system, which can not only effectively track and trace all kinds of data, but also ensure good product quality.
We offer best price, high quality Pods, Pods Touch Screen, Empty Pod System, Pod Vape, Disposable Pod device, E-cigar, Vape Pods to all over the world.
Much Better Vaping Experience!

ZGAR Vape 5.0 Pods,ZGAR Vape Pods 5.0,ZGAR Vape Pods 5.0 Pod System Vape,ZGAR Vape Pods 5.0 Disposable Pod Vape Systems
Zgar International (M) SDN BHD , https://www.sze-cigarette.com