Research on Channel of RFID System Based on OPNET
0 Preface
Radio frequency identification (Radio Frequency IdenTIficaTIon, RFID ) technology, as a non-contact automatic identification technology, can automatically identify the target object through radio frequency signals to obtain relevant data, without human contact, without optical visibility, to complete the information Input and processing, and the operation is simple and fast. In addition, because the RFID system can be technically prevented from being counterfeited and intruded, it also has extremely high security protection capabilities. However, the application of RFID technology in the actual manufacturing industry still faces some problems, such as the impact of electromagnetic interference, the probability of collision between tags is high, and the multipath interference is more serious, making the overall effect of the RFID system highly uncertain Sex.
For any communication system, the channel is an indispensable component. In the RFID system, all information is transmitted in the channel, and the quality of the channel directly affects the communication quality. Therefore, in order to improve the communication quality on the limited spectrum resources as much as possible and transmit useful information in a large capacity, the channel of the RFID system must be studied.
1 Introduction to RFID system
1.1 Composition of RFID system
One of the simplest RFID system is composed of reader, tag and computer communication network, as shown in Figure 1.
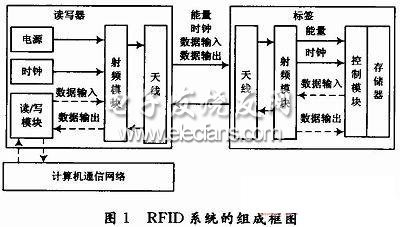
RFID tag: stores related information of the item to be identified, and is usually placed on the item to be identified. The information it stores can usually be read / written by the reader in a non-contact manner.
RFID reader: A reader is a device that can read / write tag information using radio frequency technology. The tag information read by the reader can be managed and transmitted by computer and network system.
Computer communication network: In the radio frequency identification system, the computer communication network is usually used to manage data and complete the communication transmission function. The reader can be connected to the computer communication network through a standard interface to achieve communication and data transmission functions.
1.2 Basic principles of RFID system
The working principle of the RFID system is as follows: the reader transmits a radio frequency signal of a certain frequency through the transmitting antenna. When the tag enters the working area of ​​the transmitting antenna, the tag is activated and sends its own information code through the built-in antenna. The reader obtains the tag information code and After decoding, the tag information is sent to the computer for processing. As can be seen from Figure 1, in the working process of the radio frequency identification system, energy is always used as the basis to realize data exchange through a certain timing method.
2 Introduction to OPNET
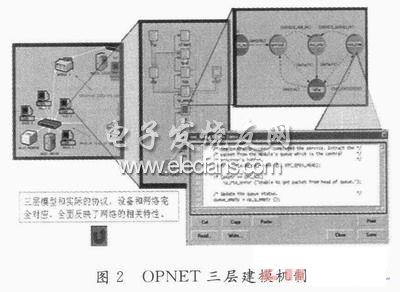
OPNET (OpTImized Network Engineering Tools) uses finite state machines to model protocols and other processes, provides core library functions, and fully supports protocol programming. The use of packet-based communication mechanisms, discrete-time driving mechanisms, and object-oriented simulation methods are ideal tools for system and network algorithm simulation. Using OPNET to simulate the RFID system network, it can intuitively simulate the communication process between the tag and the reader, and accurately establish a model that conforms to the protocol standard. At the same time, OPNET provides a wealth of testing and parameter statistics tools. OPNET uses three-layer modeling
Mechanism, the bottom layer is the Process model, and the state machine is used to describe the protocol; the second is the Node model, which is composed of the corresponding protocol modules and reflects the characteristics of the device; the top layer is the Network model, which is edited using Process Editor, Node editor, Project editor. The OPNET modeling mechanism framework is shown in Figure 2.
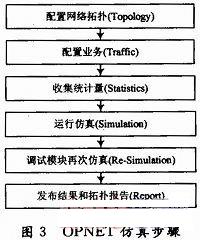
The OPNET simulation steps are shown in Figure 3.
ALLIN , https://www.nbdisplayapio.com